In order to address cybersecurity issues, a framework was developed by the National Institute of Standards and Technologies in the United States in 2014 and it was called “Framework for Critical Infrastructure Cybersecurity Version 1.0”. It looks at cybersecurity in an organization in five parts. Identify the problem areas, the information assets you want to protect; you need to protect them; you need to detect if they’ve been violated or intruded upon; then you may need to be able to respond to that intrusion; and, finally, you need to be able to recover the system.
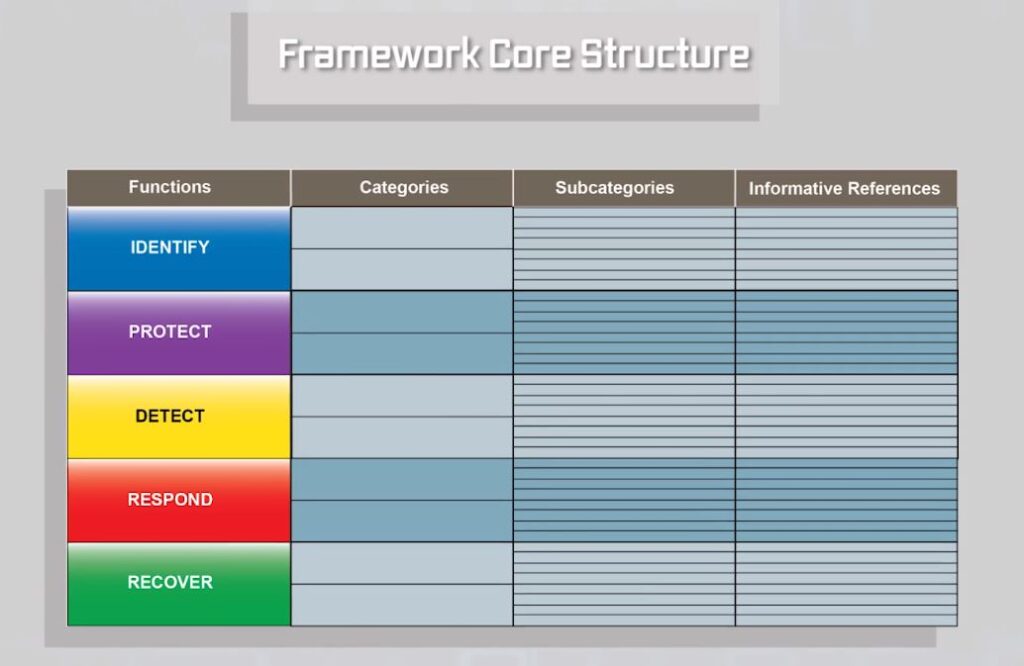
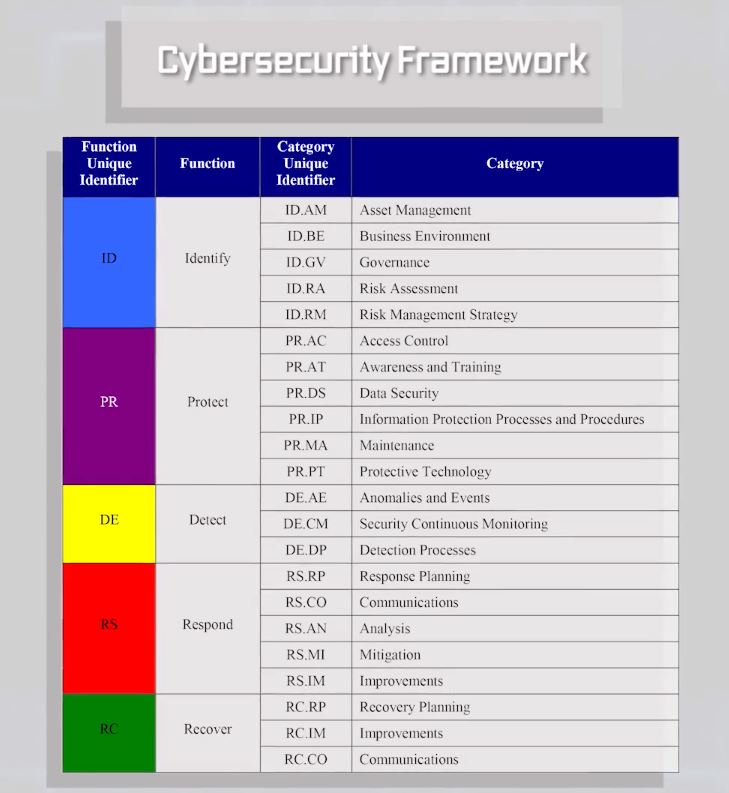
Detailed activities in each of those five functional areas are described in this graphic
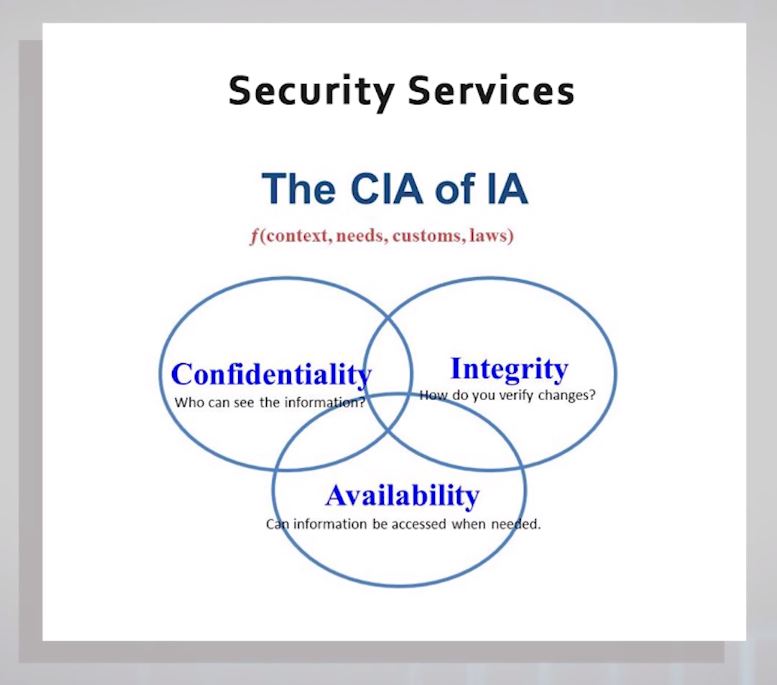
There are two basic important models that must guide one’s thinking about security controls when designing security for a system. Most people who begin their journey in cybersecurity think that cybersecurity is only about preserving secrets. It’s not only that, it’s also about maintaining data integrity and availability. It is called the CIA model
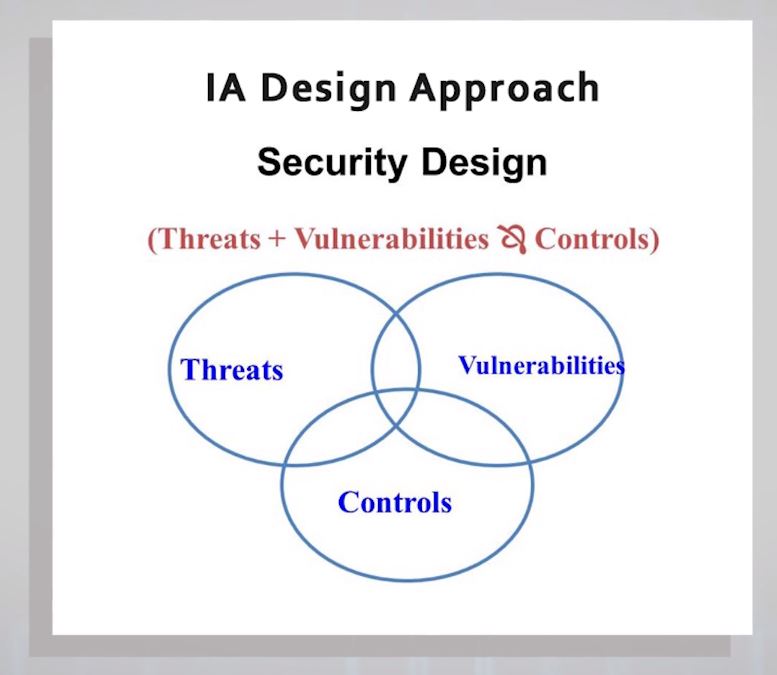
This second model looks at how we go about thinking through cybersecurity controls for systems. There’s an assessment process that requires assessing the systems that one is attempting to protect for their vulnerabilities and, at the same time, mapping threats that may be arrayed against those systems against those vulnerabilities.