In order to better understand why we need cybersecurity it is worth investigating how we got here?
How did we get here?
Back in the Agricultural age, we were tied to the land, seasons and the sun. With the Industrial Age, we introduced a lot of artificial constructs. People’s days were guided by factory whistles, they worked nine to five jobs and tended to work where the capital equipment was concentrated. So machineries were developed, steam engines were built. These ended up accumulating people, tools and resources. Then we saw the birth of corporations that hired thousands of people that were organized in a hierarchy, which in turn were organized in silos or departments such as human resource, engineering, legal, etc.
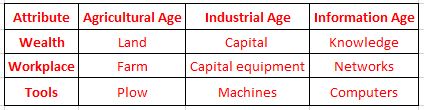
The information age brought in a whole new reality. We’re no longer tied to a desk or building. We’re interconnected virtually in work. However a closer look into our computer systems and networks reveals some interesting facts. When the information system revolution began in the 60’s, companies used mainframes. They were physically locked behind closed doors. The 80’s saw a proliferation of desktops and we were no longer tied to mainframes alone.
Soon we noticed the convenience of passing files along a wire and started wiring up our computers, systems and networks. What went unnoticed is that every network, system and node presented a possible vulnerability. We were transitioning from mainframe to desktop however, our sense of security hadn’t evolved. And so what has been unleashed by networking all of our systems is the incredible cyber security problem that we’re facing today. And a lot of it had to do with society and us as individuals having a difficult time keeping up with these changes and understanding the implications.
What are Threats?
When we first heard of mischief online, it was young kids who would stay up all night hacking into the grading system at their high school and changing grades.
Now we yearn for the good old days because we very quickly saw that organized crime began to find access to the internet and begin to squeeze out mischief makers to replace it with some serious efforts to compromise people’s finances, steal money, extort folks. Criminals began to understand that it was a lot easier to rob banks online than it was to go through the front door of a bank with a gun and risk life and limb. And the crimes got increasingly more sophisticated.
Then we saw increasingly nefarious kinds of activity online, and we began to see terrorism and nation-states begin to get engaged in activity online that would feed their national objectives. This took place over a period of about a decade and, gradually squeezed the mischief out of our concern. And we began to focus on the criminal element and the nation-state activity that was a problem.
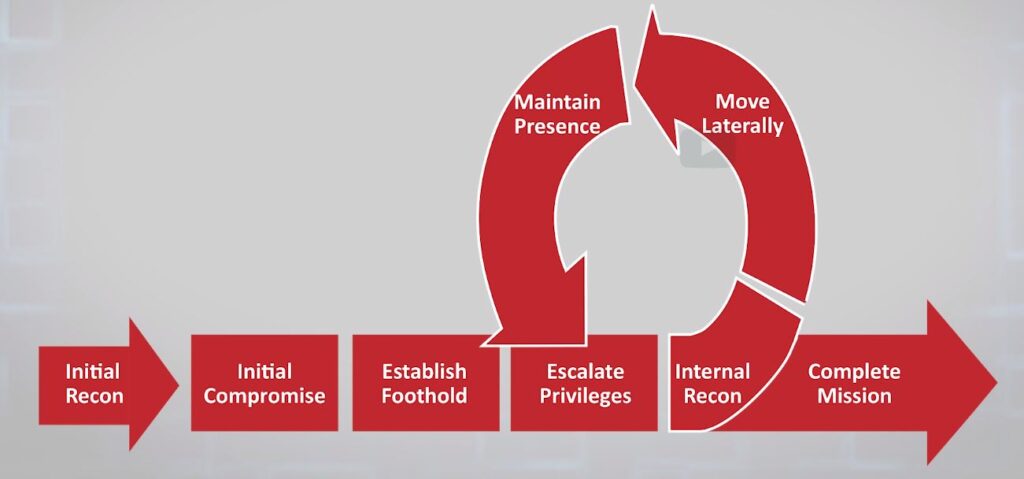
Now all of these actors have different faces. The young kid that is hacking into a system, the criminal, a nation-state adversary used similar approaches. They will do reconnaissance at the beginning of an attack, find an avenue to enter a system, stay low and slow and find a way to dig in, and then begin to navigate around the system and systems that are connected to it in order to find what they’re looking for, and then gradually exfiltrate what they’re looking for and stay over a long period of time if necessary.
Recent data breach reports indicate that the average data breach is not discovered in an organization for over 200 days, almost the better part of a year. So adversaries today have been able to disguise themselves and go unnoticed and steal, take intellectual property, gather data at will. And so this process is pretty much the same no matter who the adversary. It’s a matter of, how do we operationalize cybersecurity within our organizations to detect this activity and defend against it?